I
recently faced an authorization issue when a new BW/BEx report was created. It
wasn’t accessible by end users. When I traced in t-code RSECADMIN
I got below error message:
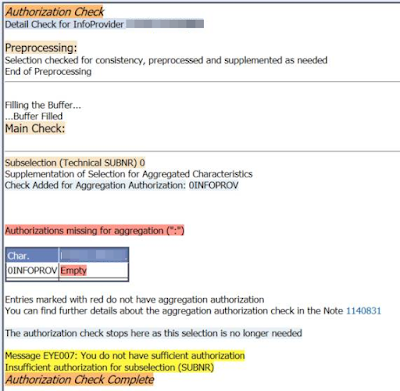
Authorization missing for aggregation
(":"): Char: 0INFOPROV – empty
From
the trace itself, it looked like it is obvious. Analysis authorization
object used in role of end user lack a 0INFOPROV characteristics. In particular
its column
aggregation. I followed up my analysis by checking corresponding analysis authorization
object.
By
definition (see e.g. here)
every analysis authorization object needs to have below three characteristics:
0TCAACTVT (activity), 0TCAIPROV
(InfoProvider) and 0TCAVALID (validity)
Therefore,
no mention of the 0INFOPROV that popped up in the RSECADMIN’s
trace. From this, it seemed that my analysis authorization object is setup in
correct way. Nevertheless, why the RSECADMIN’s
trace is complaining about 0INFOPROV? What is relation between the 0INFOPROV
and 0TCAIPROV? The latter is referenced to earlier one. However, that shouldn’t
matter...
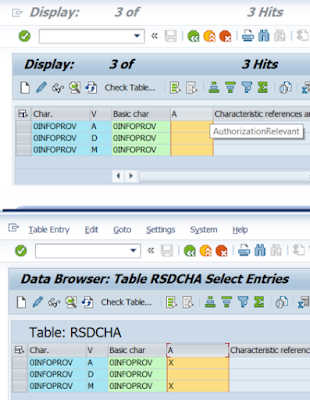
It
turned out that the 0INFOPROV was set to be an Authorization Relevant (in table
RSDCHA field AUTHRELFL is set to X). As you can see on below picture, the 0INFOPROV
comes from a Business Content as not Authorization Relevant (tables in both
systems) however in the SAP BW system in question (table at the picture’s
bottom) the active version of the characteristics was enabled as Authorization
Relevant. That particular setting was driving the security trace to mark the 0INFOPROV
as not present in the analysis authorization object. Once I included the 0INFOPROV
(and its column aggregation) into the analysis authorization object effected, business
user was able to access the report.
More information:
Defining
Analysis Authorizations
820183 - New
authorization concept in BI
1956404 -
Characteristics 0TCAIPROV, 0TCAACTVT, 0TCAVALID are no longer Authorization
Relevant after Upgrade to BW7.3 or higher